Blog
Security
/ 16 Jan, 2026Scattered Spider Tradecraft: Identity Abuse, Attack Flow, and Defense
Scattered Spider is a highly adaptive cybercrime group that breaches enterprises by abusing identity, trust, and legitimate access paths rather than malware exploits.
Learn about their identity-centric attack flow, real-world campaigns like the MGM and Caesars breaches, and how to defend against these sophisticated threats.
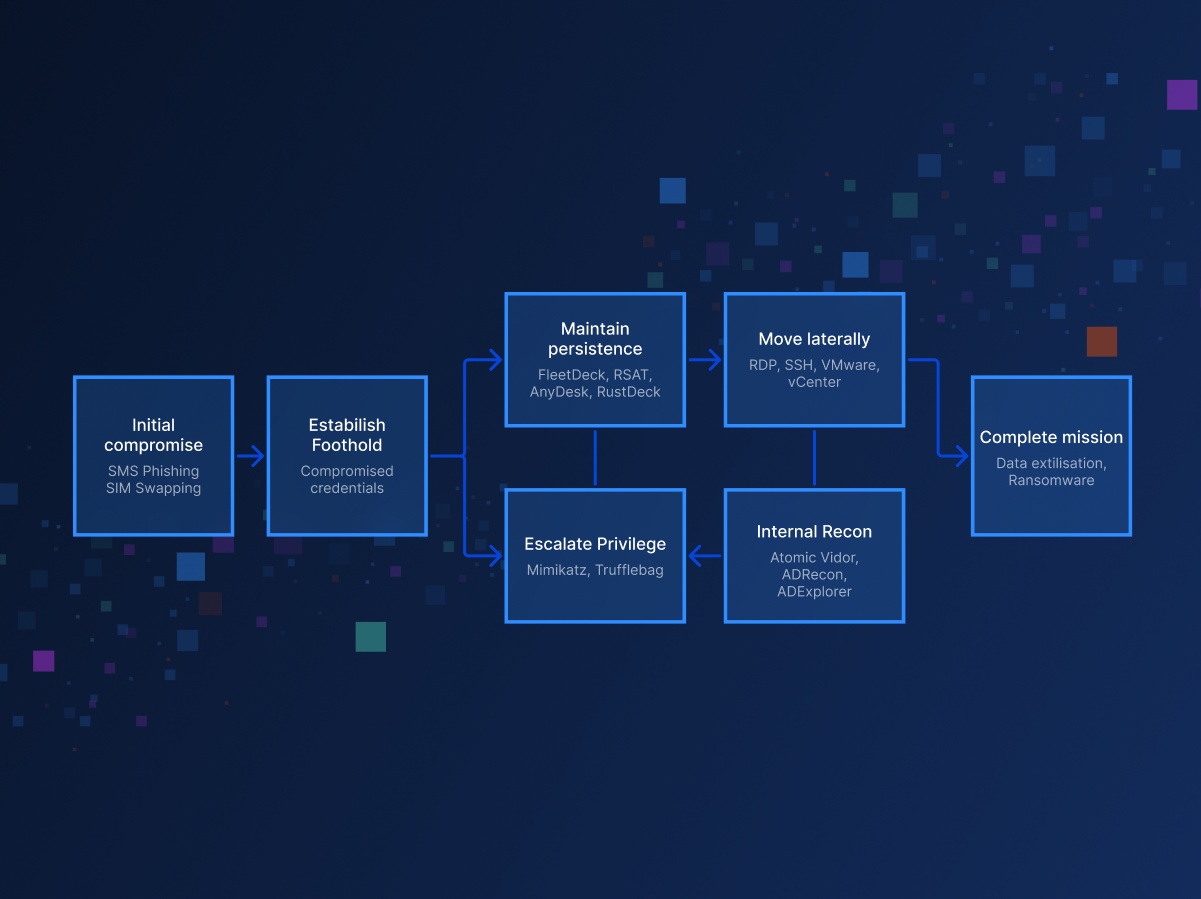
Security
/ 16 Jan, 2026Scattered Spider Tradecraft: Identity Abuse, Attack Flow, and Defense
Scattered Spider is a highly adaptive cybercrime group that breaches enterprises by abusing identity, trust, and legitimate access paths rather than malware exploits.
Learn about their identity-centric attack flow, real-world campaigns like the MGM and Caesars breaches, and how to defend against these sophisticated threats.

Security
/ 9 Nov, 2025Microsoft Actor Token Forgery
Actor Token Forgery is one of the many techniques adopted by attackers to escalate privileges and move laterally via identity vector.
This post reconstructs the attack flow, maps it to MITRE ATT&CK, and outlines immediate detection and defense actions.

Security
/ 21 Sep, 2025Access tokens strike again, the Salesloft Drift breach
In mid‑August 2025, GTIG confirmed a large‑scale credential‑harvesting and data‑theft campaign abusing trusted OAuth integrations (Drift) to access Salesforce orgs.
Attackers (UNC6395) used stolen Drift OAuth tokens to mass‑query Salesforce, mine embedded secrets (AWS, Snowflake), and pivot into connected platforms.
This post reconstructs the attack flow, maps it to MITRE ATT&CK, and outlines immediate detection and defense actions.

Security
/ 31 Aug, 2025Illicit Consent-Granting & App Backdooring – Obtaining persistence in Entra
Attackers are increasingly targeting Entra ID by silently injecting high-privilege OAuth grants and backdooring enterprise apps—achieving persistence without user interaction.
This blog provides a technical deep dive into the full attack lifecycle - initial access, consent injection, privilege escalation, and evasion.
We map each stage to MITRE ATT&CK, show real-world Graph API and CLI techniques, and outline concrete detection signals and hardening practices for defenders.

New Feature
/ 5 May, 2025Achieving Least Privilege: Unused Entitlement Removal
Unused entitlements are one of the easiest ways for an attacker to move laterally in a target environment.
However, reducing permissions is often very difficult due to availability concerns and the complexity of the permission systems.
This blog post explores how SlashID solves this problem so that customers can automatically resize identity permissions and
achieve least privilege.

Security
/ 8 Jan, 2025Protecting against malicious OAuth 2.0 applications
Several Chrome extension developers were compromised in recent weeks by an attack seeking to create a backdoor in the
extensions.
The root cause of the breach was a phishing email that leveraged OAuth 2.0/OIDC to steal
the user credentials.
This blog post explores the details of such attacks and how SlashID can help detect them and contain
the blast radius.

Security
/ 16 Dec, 2024Navigating PCI DSS 4.0: The Challenge of Non-Human Identities
The Payment Card Industry Data Security Standard (PCI DSS) has long served as the foundation for organizations handling payment card data, ensuring robust security measures are - in place to protect sensitive information
The release of PCI DSS version 4.0 on March 31, 2022, marked a significant evolution in the standard, introducing requirements and emphasizing areas that were previously under-addressed.
One such critical area is the management of non-human identities—service accounts, application accounts, APIs, and automated scripts that interact with cardholder data environments (CDE) or critical systems.
With the deadline of March 2025 fast approaching, we wrote a blog post to delves into the specific challenges companies face regarding non-human identities in PCI DSS v4.0 and - explores strategies to overcome them.
Security
/ 30 Sep, 2024Identity Security: The problem(s) with federation
Federating trust with an identity provider (IdP) is common practice to centralize identity governance.
However, attackers can exploit identity federation to breach organizations or maintain persistence in a system.
This blog post explores common attack vectors against federated identities and effective mitigation strategies.

Security
/ 16 Sep, 2024Non-Human Identities Security: Breaking down the problem
Compromised non-human identities are increasingly being leveraged by attackers to gain initial access and as a vector for lateral movement.
Microsoft, Cloudflare, and Dropbox are just a few of the companies that have fallen victim to this growing threat this year.
In this blog post, we focus on the attack vectors involved and on what actions companies must take to prevent these attacks.

New Feature
/ 26 Aug, 2024Detecting Man-in-the-Middle Attacks with SlashID
Detect when attackers access your website through malicious proxies with SlashID.


