31%
of breaches involve stolen credentials






Behavior analytics and attack-pattern matching with automated remediation actions.
Behavior analytics and attack-pattern matching with automated remediation actions.
Prevent privilege escalation, contain phishing and stop lateral movement.
Continuously right-size entitlements so each identity has only the access it needs. Clear, human-readable context makes reviews faster and more accurate.
Quickly detect and fix drift against SOC 2, ISO 27001, HIPAA, and more. Automated reporting streamlines audits and speeds up certification.
Behavioral analytics and attack-pattern matching catch anomalies instantly. Automated playbooks isolate or revoke risky access before damage occurs.
Monitor privileged identities and enforce tighter controls. Lower premiums by demonstrating reduced risk and negotiating stronger insurance terms.
of breaches involve stolen credentials
of attacks are malware-free
Kerberoasting attacks YoY
of breaches involve stolen credentials
of attacks are malware-free
Kerberoasting attacks YoY
Correlate users and NHIs across all your cloud providers, IdPs and on-prem solutions.
Label identities, credentials and resources and write your own queries to find specific events.
Identify security posture issues as well as active threats at runtime.
Implement your own risk scores and policy frameworks, tailoring security detections to your environment and reducing unwanted noise.
Easily secure on-prem, cloud, managed and unmanaged environments with SlashID connectors, workloads and browser extension.
Follow manual remediation playbooks and orchestrate automated remediation APIs through your SOAR tools.
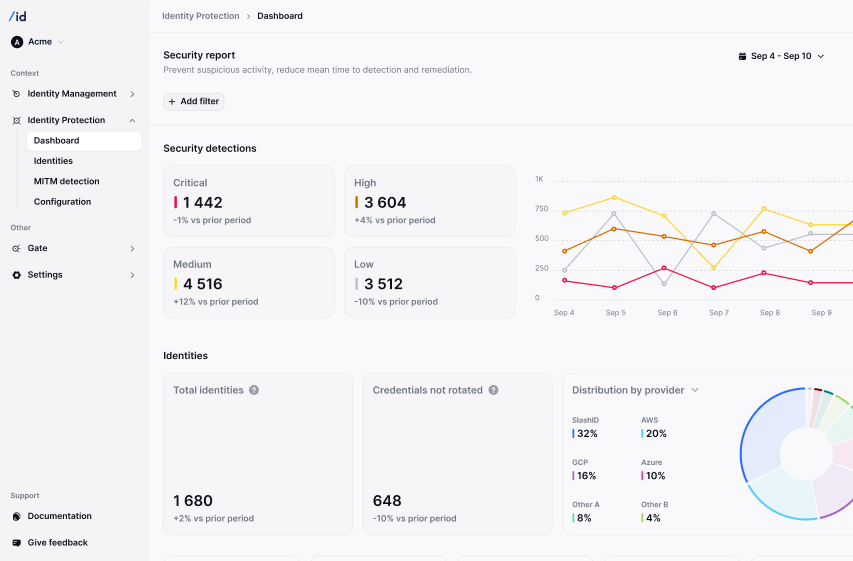
Control your environment through a single, intuitive dashboard where you can see all your identity security events.
On February 6, 2026, NYDFS issued an industry letter warning DFS-regulated entities about a spike in targeted vishing attacks where threat actors impersonate IT help desk staff to steal credentials and MFA codes. This post breaks down the technical mechanics of the campaign, why it reliably bypasses MFA, and how to detect and contain it using identity telemetry with SlashID Identity Protection, Mutual TOTP verification, and MITM detection.


Scattered Spider is a highly adaptive cybercrime group that breaches enterprises by abusing identity, trust, and legitimate access paths rather than malware exploits. Learn about their identity-centric attack flow, real-world campaigns like the MGM and Caesars breaches, and how to defend against these sophisticated threats.


Actor Token Forgery is one of the many techniques adopted by attackers to escalate privileges and move laterally via identity vector. This post reconstructs the attack flow, maps it to MITRE ATT&CK, and outlines immediate detection and defense actions.

