Discover Identity Risk
Build a unified, always-current view of your entire identity attack surface and uncover your most critical risks.
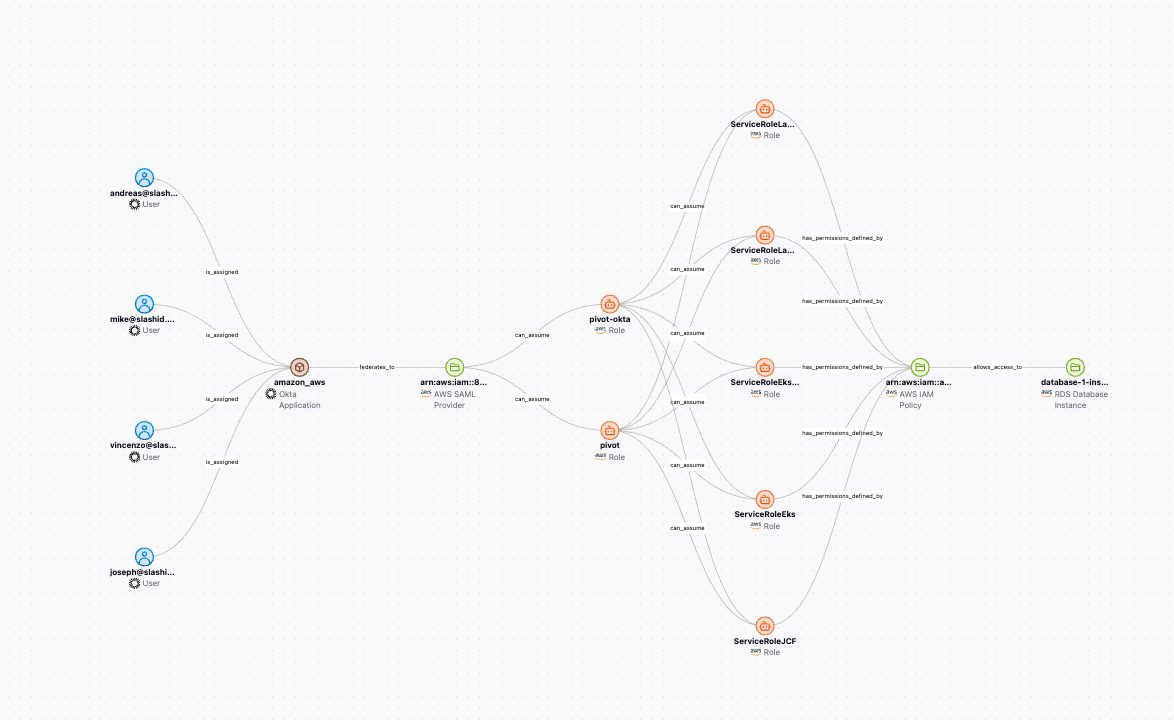
Identities and credentials sprawl across AD, cloud providers and SaaS creating hidden risks that fall through the cracks of siloed tools. SlashID's unified identity inventory sees everything (human + non-human), detects active threats and posture issues the moment they appear, and ranks risks by blast-radius so teams can act first on what matters most.
Benefits
How it helps
Complete inventory
of human & non-human identities across every environment.
Real-time detection
for unfederated apps, orphan accounts, stale keys and toxic role paths.
Risk-based prioritisation
findings scored with privilege graph context, not raw alert volume.
Deep visibility
provides critical insights into fine-grained access & permissions
Easy to deploy
How it works
Ready to discover your identity risks?
Get a unified view of your identity attack surface and start protecting what matters most.