Automate Compliance Gap Analysis
Compare live access & identity data against regulatory requirements and generate audit-ready evidence on demand.
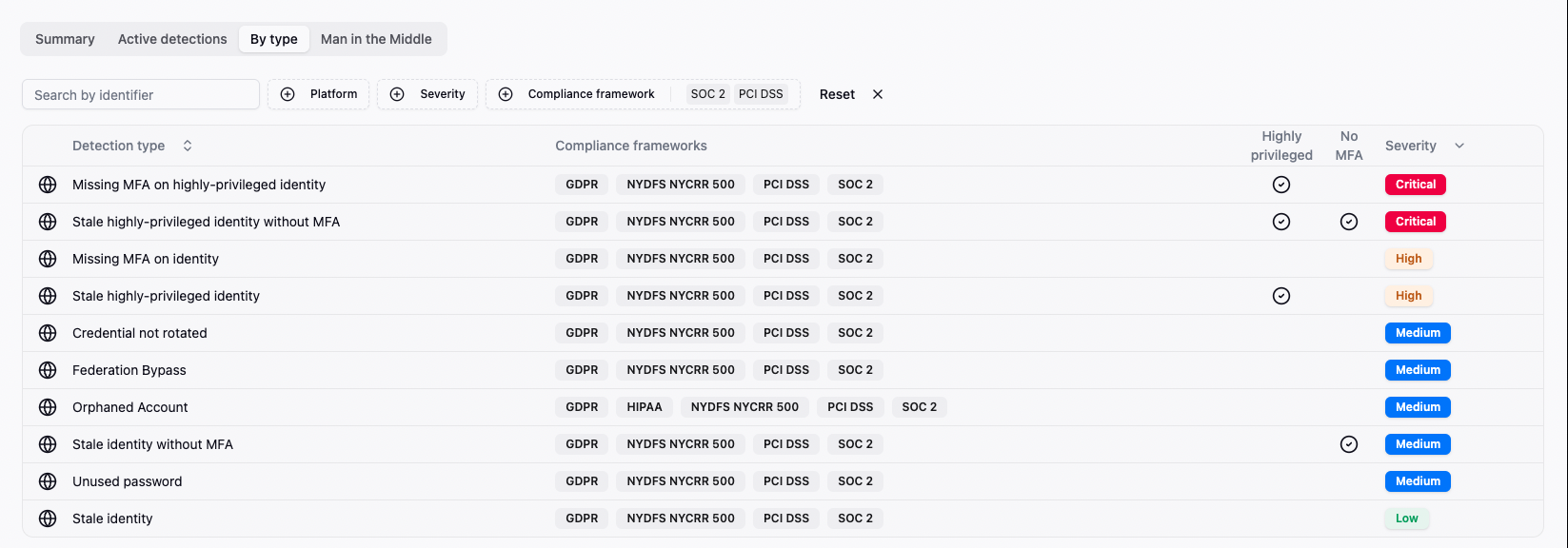
Audits drain weeks of time and resources, yet static reviews still miss issues between assessments. SlashID's live control mapping highlights gaps against SOC 2, PCI-DSS, GDPR and more, routes tasks to owners, and exports evidence in clicks—no need for spreadsheets and manual evidence collection.
Benefits
How it helps
Continuous gap mapping
against external and internal standards.
Task automation
pull-request-style tickets turn observations into tracked work.
Instant evidence export
satisfies auditors without manual collection.
Hundreds of hours saved
thanks to our natural language interface. Your analysts can collect evidence without any IAM knowledge.
Ready to start a top-tier security upgrade?
Streamline your compliance processes with automated gap analysis and audit-ready evidence generation.