Secure Non-Human Identities & AI Agents
Discover, govern and rotate credentials for service accounts, workloads, AI agents, and automation pipelines.
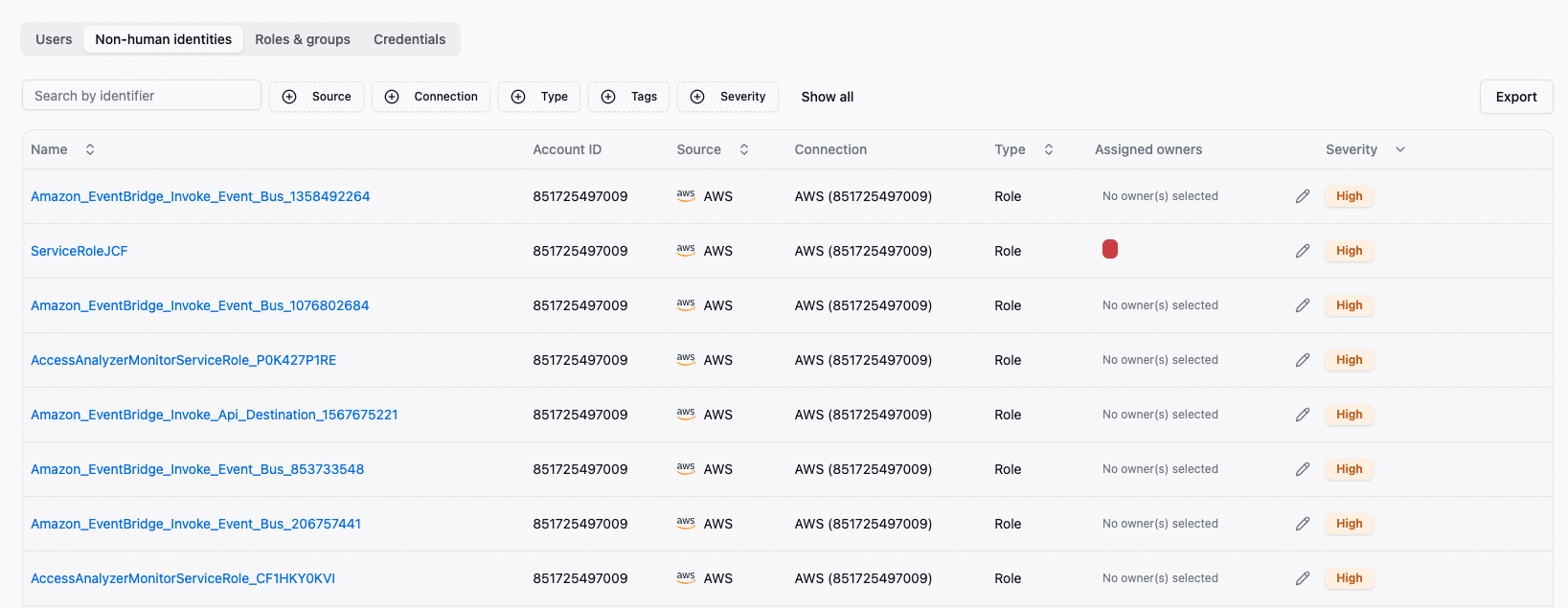
Service accounts, API keys, secrets, workloads, and AI agents outnumber humans yet organizations have little to no oversight of these critical assets. SlashID provides unified coverage across all identity types—human, non-human, and AI agents—with cross-environment visibility, risk scoring, and automated remediation to keep every credential in line with least-privilege policies, short-lived and fully tracked.
Benefits
How it helps
Complete identity inventory
human users, service principals, API keys, AI agents, and secrets with resource reachability.
Risk flags
for long-lived keys, hard-coded secrets and unused service accounts.
Automated rotation
to short-lived, least-privilege roles.
Continuous assurance
monitors and right-sizes access as environments scale.
Ready to start a top-tier security upgrade?
Secure all your identities—human, non-human, and AI agents—with comprehensive discovery, risk assessment, and automated credential management.