Identity Security Posture Management
Continuously measure, visualize and improve identity-centric security posture across multi-cloud and on-prem environments.
Siloed tools allow misconfigurations, risky access paths, and toxic combinations to slip through the cracks. Blast radius balloons as a result and adversaries are more than happy to take advantage of these mistakes. SlashID gives teams a full view of their identity attack surface, identifies your most critical posture risks, then guides remediation through our automated workflows or actionable recommendations.
Benefits
How it helps
Deep queries
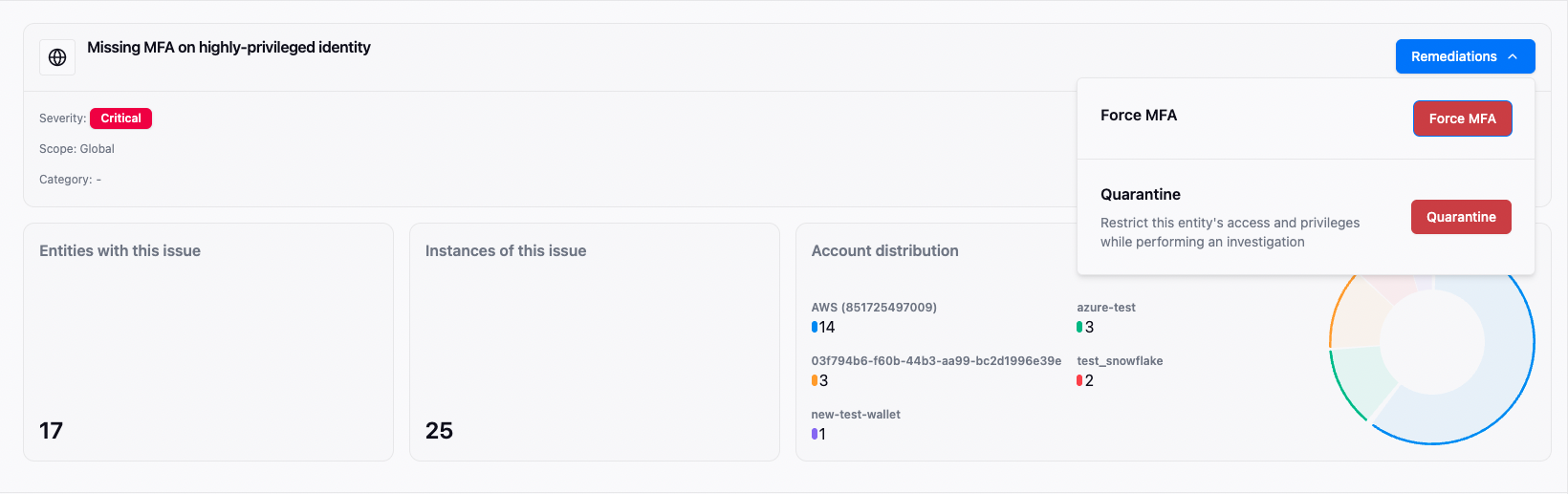
reveal SoD violations, missing MFA, and privilege creep.
Drift alerts
fire when new resources break guardrails.
Guided fixes
click or leverage our APIs to remediate without leaving the dashboard.
Ready to start a top-tier security upgrade?
Improve your identity security posture with comprehensive monitoring and automated remediation.