Identity Threat Detection & Response
Stop identity-based attacks—from phishing & credential stuffing to privilege escalation—in real time, everywhere identities live.
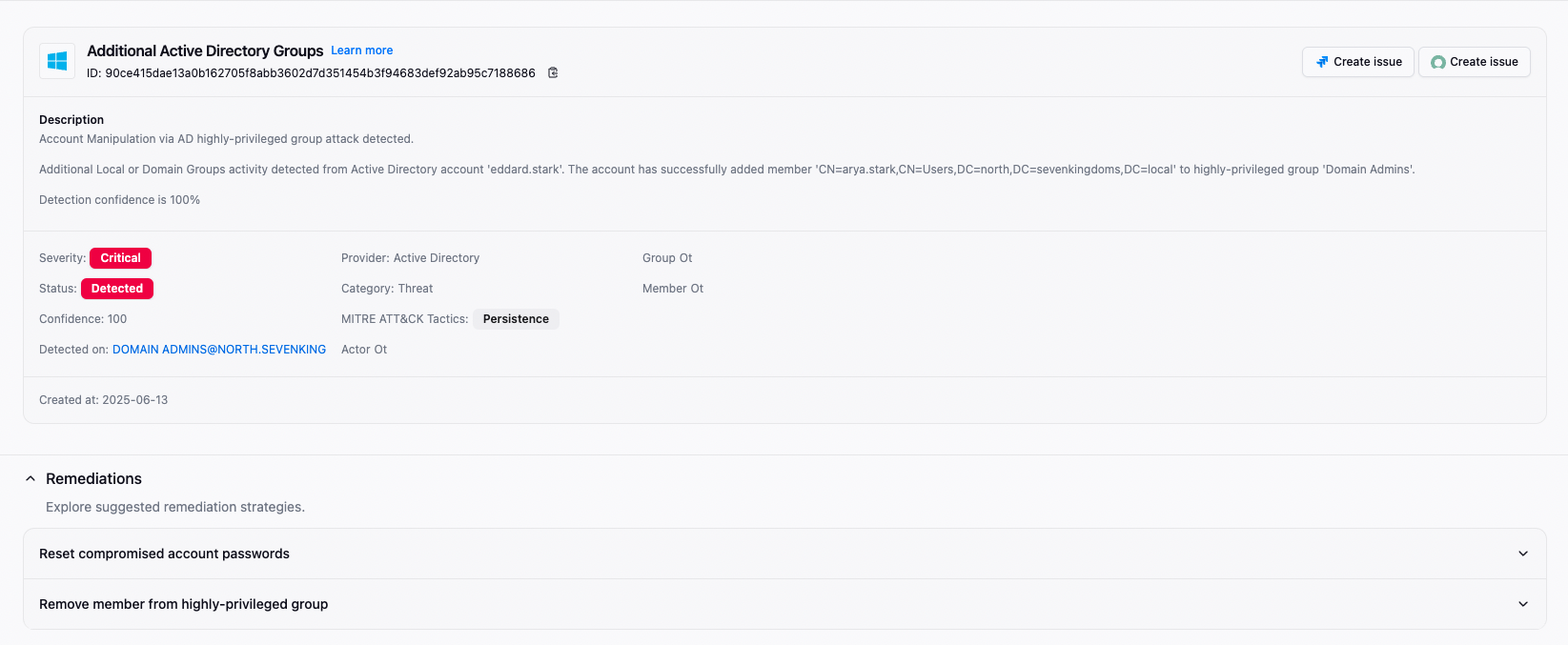
Phishing, credential stuffing and privilege escalation attacks strike faster than traditional tools can correlate events. SlashID’s real-time detections and behavioral analytics spot account takeover or insider drift the instant behavior deviates, then revoke sessions and trigger IR workflows before attackers reach crown-jewel data.
Benefits
How it helps
Real-time watch
on logins, tokens and keys across IdP, cloud, on-prem and SaaS.
Behavioral detection
for ATO, push-bombing, lateral-movement and insider misuse.
Auto-containment
kill sessions, force step-up auth, open IR tickets with full context.
Seamless SIEM/SOAR integration
via read-only connectors—no proxies or agents.
Ready to start a top-tier security upgrade?
Stop identity-based attacks before they reach your crown-jewel data with real-time threat detection.